We added a bunch of important improvements to Mashery Traffic Manager recently that really rounds off our support for a very important industry standard CORS. Hope you find them useful !
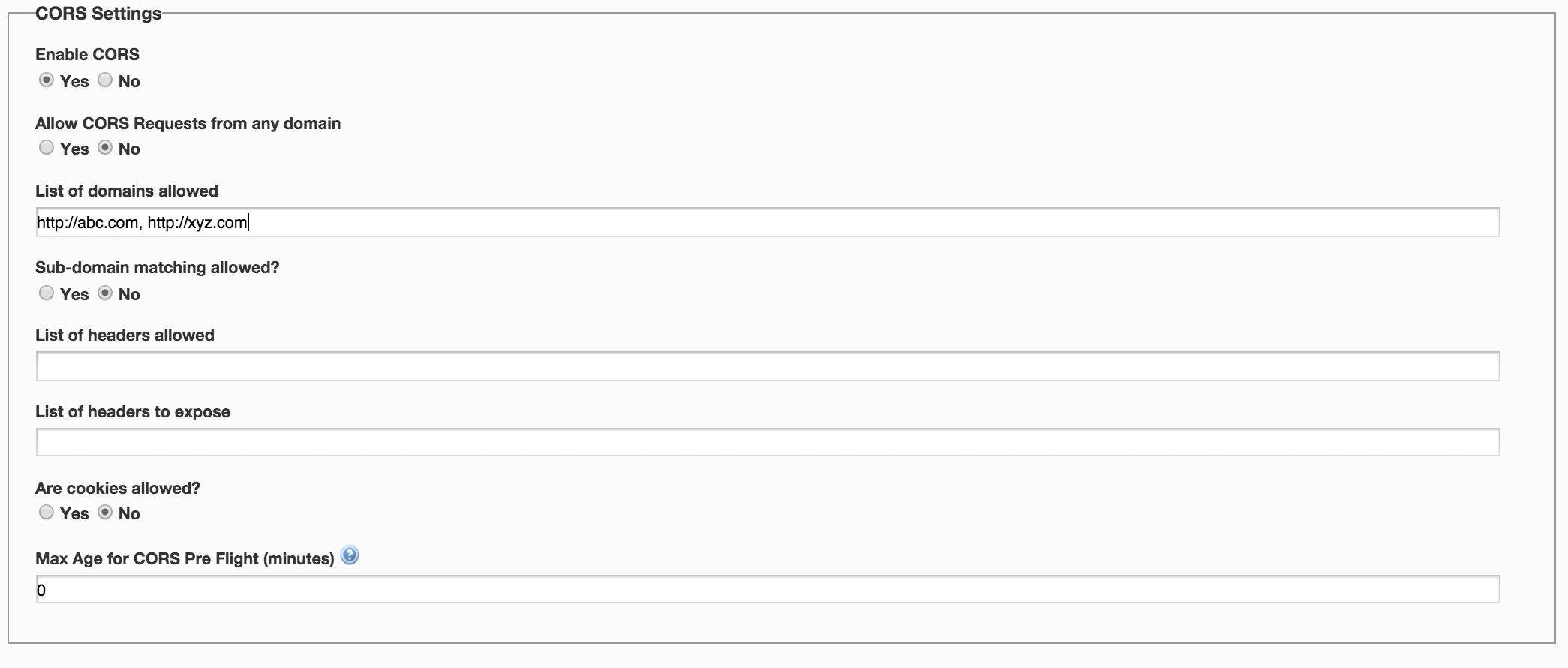
- If Allow requests from any domain is set to No on the Dashboard then:
- The API administrator can specify a comma separated "List of domains allowed". The requests made from domains that are not in the list are denied.
- To allow for more flexibility, API administrator can also select if "Sub-domain matching allowed" is Yes. By default, exact domain matching process is followed.
- In case of an exact domain match, for e.g. if http://abc.com, is specified in the “List of domains allowed”, only requests for http://abc.com are allowed.
- In case of a sub-domain match, for example, if http://abc.com is specified in the “List of domains allowed” on the Dashboard, requests coming from http://abc.com, http://xyz.abc.com and http://xxx.abc.com are accepted as valid and allowed through
- Note that in either of the above cases, http://abc.com, https://abc.com, and http://abc.com:8080 are not considered identical and are never matched
- CORS specification does not allow any custom header to be processed by the browser client application except if the server explicitly white-lists those headers via Access-Control-Expose-Headers. With the "List of headers to expose" field, API administrator can white-list the headers that Traffic Manager will add to Access-Control-Expose-Header in the response.
- API administrator can specify a comma separated "List of headers allowed". These are used to validate against values in Access-Control-Request_Header and determine if the request can be allowed through or not. If allowed, corresponding headers are added to Access-Control-Allow-Header back in the response. If this field is left empty, any incoming header is allowed – this is to maintain backward compatibility
- API administrator can specify whether cookies are allowed for the CORS requests or not. By default, cookies are not allowed. If cookies are allowed, Access-Control-Allow-Credentials is set to true on the preflight response and CORS response.
- To facilitate debugging scenarios for CORS request and response, any selected Mashery specific debug headers are white-listed via Access-Control-Expose-Headers so that the client application can process the response appropriately. Specifically if Include X-Mashery-Responder Header in Response, and Include X-Mashery-Message-ID Header in Response are selected on the end-point settings in the dashboard, these will be added to Access-Control-Expose-Headers list
- Even in the case of error responses, CORS specific headers are added in the response. This allows the client application to read and process the right error message
- Even if pre-flight request fails, it is returned with a 200 code but with the right error message This will ensure that the client application can process and display the appropriate error message on the browser which facilitates better debugging.